How to Browse Anonymously With Tor ?
What is Tor?
Tor is free software and an open network that helps you defend against a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security known as traffic analysis
Why Anonymity Matters ?
Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location. Tor works with many of your existing applications, including web browsers, instant messaging clients, remote login, and other applications based on the TCP protocol.
HOW TOR WORKS?

First, the client’s Tor-enabled software determines the list of available Tor nodes that are present in the network. By doing so, it ensures a random node selection each time so that no pattern can be observed by anyone spying, ensuring that you remain private throughout your activities. Random path selection also leaves no footprints, as no Tor node is aware of the origin or destination other than the terminal ones receiving from the clients. And since, from the millions of Tor nodes available, any one can act as the first receiving node, therefore it is virtually impossible to trace the origin.

Now, the client generates an encrypted message which is relayed to the first Tor node. The Onion router on this node would peel off one layer of encryption and read the information identifying the second node. The second node would repeat the same process and pass on to third. This would go on until the final node receives the location of the actual recipient, where it transmits an unencrypted message to ensure complete anonymity.

Finally, when the client computer wants to establish another path, suppose to visit another website, or even the same one, the Tor network will select an entirely different, random path this time.
( Read more on https://www.torproject.org/about/overview.html.en)
How to Install TOR ?
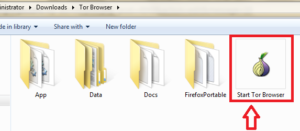
Download and extract Zip file on your computer then click on the Start Tor Browser option.
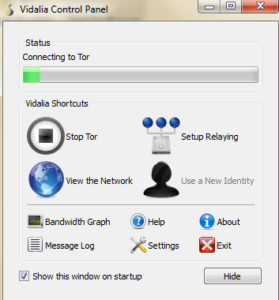
it will connect with Tor network
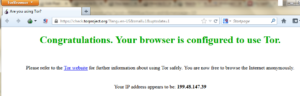
then Tor browser will open
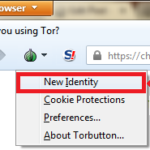
click on the new Identity option to change your identity.
Is Tor Really Anonymous and Secure?
Tor is not the perfect anonymity and privacy solution. It has several important limitations and risks, which you should be aware of if you’re going to use it.
If you’re accessing an encrypted (HTTPS) website such as your Gmail account, this is okay – although the exit node can see that you’re connecting to Gmail. if you’re accessing an unencrypted website, the exit node can potentially monitor your Internet activity, keeping track of the web pages you visit, searches you perform, and messages you send.
When using Tor, be sure to use encrypted (HTTPS) websites for anything sensitive. Bear in mind that your traffic could be monitored – not just by governments, but by malicious people looking for private data. ( check my article Encrypt Your Web Browsing with HTTPS Everywhere
For More Privacy check my articles :-
Encrypt your Live Chat with Cryptocat
How to encrypt your cloud storage for free
Send notes that will self-destruct after being read
How to Stop Trackers From Tracking You Online
How to always start Google chrome in Private browsing mode
Hide your Real IP Location and Browse Anonymously
Encrypt Your Web Browsing with HTTPS Everywhere
How to Encrypt Your Email with Mailvelope
Hope you like my post.How to Browse Anonymously With Tor. Please Share with others.