Secure your network for Most common Attacks with Checkpoint Firewall :-
Securing network is always night-mare for IT-administrators but present day most of the firewall’s vendor’s like checkpoint , Cisco, Paloalto etc.. are providing prevention on most common attacks like DOS attack, SYN-Flood attack, IP-Spoofing, Man-in-the Middle attack, Port scanning , Malicious IP’s , DNS Cache Poisioning , Application layer attacks like SQL Injection , Cross site scripting etc.
Today i am going to show you How to prevent Common attacks with Checkpoint Firewall ( GAIA R 77 ) . 🙂
Checkpoint GAIA comes with a Software blade of IPS that provide the protection against most network attacks. You have to enforce IPS protection on your particular gateways.
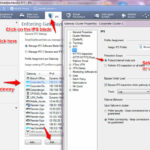
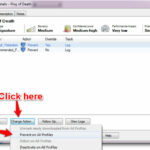
Open Checkpoint Smart Dashboard and navigate to IPS blade option. Click on the Enforcing Gateways option and select your gateway and click on the Edit option and select the Recommended or Default protection in Assign IPS profile option. In protection Scope, either select Protection internal Host only or perform IPS inspection on all traffic.
Protection against SYN Flood Attack :-
A SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN requests to a target’s system in an attempt to consume enough server resources to make the system unresponsive to legitimate traffic.
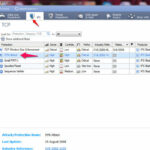
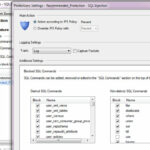
To provide protection against SYN Flood attack, navigate to Protections > By protocol > IPS Software Blade > Network Security > TCP
In the Right-pane select the SYN Flood signature,
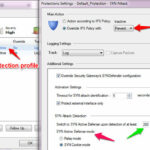
then double-click on it, In general tab, select your protection profile, and click on the Edit option and select the ” Override IPS policy with Prevent option. In the SYN Attack Detection option you have option define number of SYN packets per timeout. Also select the active defense mode to SYN cookies.
Protection against DOS attack :-
A type of attack on a network that is designed to bring the network to its knees by flooding it with useless traffic. Many DoS attacks, such as the Ping of Death and Teardrop attacks, exploit limitations in the TCP/IP protocols.
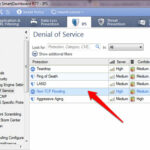
To provide protection against like Ping of Death, LAND , Teardrop, Non-TCP flooding, navigate to Protections > By protocol > IPS Software Blade > Denial of Services.
Select signatures and enable on your gateway.
You have also option to enable protection on all profiles. To do so click on the Change option tab and select the ” Prevent on all profile ” option.
Related articles :-
How to Prevent Dos attacks with WatchGuard XTM Firewall
Configuring connection limit on Cisco ASA and CheckPoint Firewall
Find Out if Your Computer is Infected with a Bot
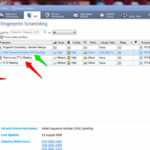
Protection against Man-in-the Middle attack and OS Fingerprinting :-
Fingerprinting is a technique by which a remote host gathers information about a host or network by looking at the unintentional side effects of the communication.
Techniques involve either active fingerprinting, by which the adversary sends slightly off-protocol packets and tries to pick up information from the responses (or their lack of), and passive fingerprinting, by which the adversary either generates no traffic at all (and relies on passively received traffic), or generates only 100% standard traffic.
To provide this protection, navigate to Protections > By protocol > IPS Software Blade >Network Security > Fingerprint Scambling. and enable the Initial Sequence Number ( ISN ) Spoofing and Time to Live Masking.
Related Articles :-
How To do Man in Middle Attack using Ettercap in Kali Linux
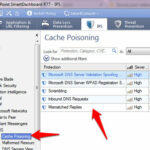
Protection against DNS Cache poisoning :-
DNS cache poisoning, also known as DNS spoofing, is a type of attack that exploits vulnerabilities in the domain name system (DNS) to divert Internet traffic away from legitimate servers and towards fake ones.
To provide this protection, navigate to Protections > By protocol > IPS Software Blade >Application Intelligence > DNS > DNS Cache Poisioning and enable the below mentioned signatures.
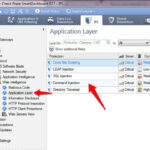
Protection against SQL Injection , XSS attack and Directory Attack :-
Cross-site scripting :-
Cross-site scripting attacks place malicious code in locations where other users see it. The intention of the attack is to steal cookies that contain user identities and credentials, or to trick users into supplying their credentials to the attacker. Scripting code includes tags such as <SCRIPT>. The code can instruct the server to send its cookies to another location, such as another web site (hence the name: Cross Site Scripting), where the hacker can see the cookies.
SQL injection :-
SQL injection attacks allow a remote attacker to execute SQL commands disguised as a URL or form input to the database. A successful attack may get the database to run undesirable commands. This could cause damage by revealing confidential information, modifying the database, or even shutting it down.
Directory traversal :-
Directory traversal attacks allow hackers to access files and directories that should be out of their reach. This can for example allow viewing of directory listings, and in many attacks, could lead to running executable code on the web server with one simple URL.
To provide protection against this attacks, navigate to Protections > By protocol > IPS Software Blade > Web Intelligence > Application layer.
here , you have also option to define own parameters.
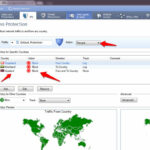
Geo – Protection :-
Geo Protection, lets you control network traffic for specified countries. An IP-to-country database connects packet IP addresses to the countries. Configure one set of policies for each Profile to block or allow traffic for one or more countries. Configure a different policy that applies to the other countries. Private IP addresses are allowed unless the other side of the connection is explicitly blocked. Check Point control connections (such as between Security Gateways and the Security Management Server) are always allowed, regardless of the Geo Protection policy.
Configure the Geo Protections for each of the IPS Profiles separately. Policies with a Block action forSpecific and Other Countries are only enabled when the Profile Action is set to Prevent.
Zero-day Attack Prevention :-
Check Point ThreatCloud Emulation Service prevents infections from undiscovered exploits, zero-day and targeted attacks. This innovative solution quickly inspects files and runs them in a virtual sandbox to discover malicious behavior. Discovered malware is prevented from entering the network.
Hope you like my post. Please Share with others.
Also Check :-