An Introduction to Cisco ASA Firewall :-
Is the ASA a firewall? Yes. Is it more than a firewall? Yes! 🙂
The Cisco Adaptive Security Appliance (ASA) is a versatile device that is used to secure a network. To preserve the integrity and stability of resources on a network, they must be protected from things that can’t always be trusted or controlled. The firewall must inspect traffic at Layer 4 so that any new sessions that are negotiated as part of an existing connection can be validated and tracked.
The Cisco ASA platform has the capability to perform any of the firewall techniques described in the An Introduction to Network Firewalls Technologies. Even further, the ASA has many features that go beyond the basic firewall techniques, giving it great versatility.
previously i written about Cisco Router, Watchguard Firewall. from today i am going to write about Cisco ASA features and many-many topics on cisco ASA. You can also check my cisco ASA articles on ccnpsecurity.blogspot.com . 🙂
In this article, i am going to show you Cisco ASA features. 🙂
Cisco ASA features:-
Stateful packet filtering engine:-
The SPF engine tracks connections and their states, performing TCP normalization and conformity checks, as well as dynamic session negotiation.
Here is some of the information that a stateful firewall keeps in its state table:-
- Source IP address
- Destination IP address
- IP protocol (like TCP or UDP)
- IP protocol information, such as TCP/UDP port numbers, TCP sequence numbers, and TCP flags
Note :- The security appliances provide a stateful process for TCP and UDP traffic only, by default. Starting in version 7, ICMP can also be treated statefully, but this is disabled by default.
Note :- A stateful firewall maintains the connection table. If it sees a connection teardown request between the source and destination, the stateful firewall removes the corresponding connection entry. If a connection entry is idle for a period, the entry will time out, and the stateful firewall will remove the connection entry.
Sequence Number Randomization :-
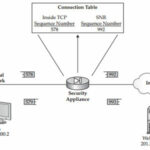
The security appliances include a security feature called Sequence Number Randomization(SNR), which is implemented by the security algorithm. SNR is used to protect you against reconnaissance and TCP session hijacking attacks by hackers. One problem with the TCP protocol is that most TCP/IP protocol stacks use a fairly predictable method when using sequence numbers—a sequence number in a TCP segment indicates the number of bytes sent. With many connection types, a hacker can use this information to make predictions concerning the next set of data to be sent, and thus the correct sequence number. Sophisticated hackers will then use this information to hijack the session.
The security appliance’s SNR feature addresses this problem by randomizing the TCP sequence numbers that the TCP/IP application places in the TCP segment header. The security appliance will place the old sequence number as well as the new sequence number in its conn table. As traffic is returned from the destination, through the appliance, back to the source, the appliance looks for this information and changes it back for acknowledgment purposes.
A TCP segment might pass through the security appliance where the sequence number is 578 in the segment, as shown in above Figure. The SNR changes this sequence number to a random number and places it in the state table (992 in this case), and forwards the segment to the destination. The destination is unaware of this change and acknowledges to the source the receipt of the segment, using an acknowledgment number of 993. The appliance, upon receiving the reply, undoes the SNR process by changing the 993 value to 579, so that the source device is not confused. Remember that the TCP acknowledgement process has the destination increase the sequence number by one and uses this as the acknowledgment number.
Note :- TCP Sequence Number Randomization is providing the security against man-in-the-middle attack and OS fingerprinting.
Related Articles :-
How To do Man in Middle Attack using Ettercap in Kali Linux
How to Find all domains on same IP address
Network Attack Prevention :-
The security appliances support a handful of network attack prevention features:-
- Threat detection
- TCP normalization
- Connection limits and timeouts
- IP spoofing prevention
With threat detection, the appliance monitors the rate of dropped packets and security events, which can be caused by matches on ACL deny statements, receiving invalid packets, exceeding connection limits (total connections and TCP connections that don’t complete the initial three-way handshake), detecting denial of service attacks, receiving suspicious ICMP packets, overloading interfaces, detecting a reconnaissance scan, and many other factors. When a threat is detected, a log message is generated.
The TCP normalization feature lets you specify matching criteria that identify abnormal TCP packets, which the security appliance drops when detected. TCP normalization is implemented using the Modular Policy Framework .TCP normalization can identify and prevent inconsistent TCP retransmissions by validating TCP checksums, allowing or dropping TCP segments that exceed the maximum segment size (MSS), limiting the number of out-of-order packets for a connection, dropping SYN segments with data, and handling many other abnormalities with TCP transmissions.
Cisco supports a TCP Intercept feature that allows you to place limits on the number of complete and/or half-open connections. A half-open connection is one that has not completed the initial three-way handshake: SYN, SYN/ACK, and ACK. This feature can be used to defeat or greatly limit the effect of a TCP SYN flood attack.
Related Articles :-
How to View SYN-Flood attack using the Command Prompt
Perform DDOS Attack with Hping Command
How to Prevent Dos attacks with WatchGuard XTM Firewall
Configuring connection limit on Cisco ASA and CheckPoint Firewall
Application inspection and control:- The AIC function analyzes application layer protocols to track their state and to make sure they conform to protocol standards.
User-based access control:- The ASA can perform inline user authentication followed by Cut-through Proxy, which controls the access that specific users are allowed to have. Once a user is authenticated, Cut-through Proxy also accelerates inspection of a user’s traffic flows.
The user connections are not typically authenticated by the appliance itself, but by an external security server, such as the Cisco Secure Access Control Server (CSACS).
Cisco supports both the TACACS+ and RADIUS protocols for authentication. The CTP feature on an appliance can authenticate the following connection types:-
- FTP
- HTTP and HTTPS
- Telnet
Session auditing:- Accounting records can be generated for user-based sessions, as well as for application layer connections and sessions.
Security Services Modules:- The ASA platform supports several Security Services Modules (SSM) that contain specialized hardware to offload processor-intensive security functions. An ASA can contain one SSM, offloading either IPS or content security services.
Reputation-based Botnet Traffic Filtering:- An ASA can detect and filter traffic involved with botnet activity on infected hosts. The Botnet Traffic Filter database used to detect botnet threats is periodically updated by Cisco. Chapter 9covers Botnet Traffic Filtering in more detail.
Category-based URL filtering :- An ASA can leverage an external URL filtering server to enforce acceptable use policies and control user access to various types of web services.
Cryptographic Unified Communications (UC) proxy:- When Cisco Unified Communications traffic must pass through an ASA, the ASA can be configured as an authorized UC proxy. The ASA can then terminate and relay cryptographically protected UC sessions between clients and servers.
Denial-of-service prevention:- An ASA can leverage traffic-control features like protocolnormalization,trafficpolicing,andconnectionratecontrolstominimize the effects of denial-of-service(DoS)attacks.
Traffic correlation:- The threat detection feature examines and correlates traffic from many different connections and sessions to detect and block anomalies stemming from network attacks and reconnaissance activity.
Remote access VPNs:- An ASA can support secure VPN connections from trusted users located somewhere on an untrusted network. Clientless SSL VPNs can be used to offer a secure web portal for limited remote access to users, without requiring VPN client software. For complete secure network access, full tunneling of all user traffic is supported with either SSL VPNs or IPsec VPNs, which require VPN client software.
Site-to-site VPNs:- An ASA can support IPsec VPN connections between sites or enterprises. Site-to-site or LAN-to-LAN VPN connections are usually built between firewalls or routers at each location.
High availability failover clustering:- Two identical ASA devices can be configured to operate as a failover pair, making the ASA security functions redundant in case of a hardware failure.
Redundant interfaces:- To increase availability within a single ASA, interface scan be configured as redundant pairs so that one is always active, while the other takes over after an interface hardware failure.
Ether Channel:- Multiple ASA interfaces can be aggregated or bundled together as a single logical interface. By connecting an Ether Channel between an ASA and a switch, you can scale the bandwidth and offer additional redundancy.
Traffic and policy virtualization :- An ASA can be configured to operate multiple virtual instances or security contexts, each acting as an independent firewall. Each virtual context has its own set of logical interfaces, security policies, and administrative control.
Rich IP routing functionality :- An ASA can forward traffic onto the local networks connected to each of its interfaces without any additional IP routing information. It can also be configured to use static routes or a dynamic routing protocol such as RIPv1, RIPv2, EIGRP, and OSPF to make more complex routing decisions.
Powerful Network Address Translation (NAT) :- As an ASA inspects and forwards packets, it can apply a rich set of NAT functions to alter source and destination addresses.
Transparent (bridged) operation :- An ASA can be configured to operate as a transparent firewall, effectively becoming a secure bridge between its interfaces. Transparent firewall mode allows an ASA to be wedged into an existing network without requiring any readdressing of the network.
Integrated DHCP, DDNS, and PPPoE:- An ASA can be configured to act as a DHCP client or a PPP over Ethernet (PPPoE) client to obtain a dynamic IP address for its interfaces from the network, and as a Dynamic DNS (DDNS) client to record information for hostname-to-address resolution. As well, an ASA can act as a DHCP server to offer IP addressing services to other hosts on the network.
IPv6 support:- An ASA can be configured to operate natively in an IPv6 network.
IP multicast support:- An ASA can leverage the Internet Group Management Protocol (IGMP) and the Protocol Independent Multicast (PIM) protocol to participate in handling IP multicast traffic.
Management control and protocols :- An ASA supports several different methods of management control, including a console port, Telnet, Secure Shell (SSH), Secure HTTP (HTTPS), and Simple Network Management Protocol (SNMP; Versions 1, 2c, and 3). A dedicated out-of-band management port is also available. An ASA can send event notifications using SNMP traps, NetFlow, and syslog.
Simple software management :- An ASA supports a local file system and remote file transfers for software upgrades. Software upgrades can be performed manually, automatically, or in a zero-downtime fashion on a failover cluster of ASAs.
Configuration flexibility and scalability:- Security policies and rules can be configured using reusable objects. Through the Modular Policy Framework (MPF), security features can be configured and applied in a flexible and versatile manner.
Cisco Security Management Suite:- Multiple ASAs can be managed from the Cisco Security Management Suite for ease of administration.
ASA 5510/5520/5540/5550 : Front Panel
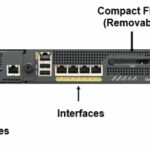
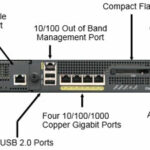
ASA 5510/5520/5540/5550 : Back Panel
ASA 5510/5520/5540/5550 : Back Panel Connections
Security Services Module :-
- High performance module designed to provide additional security services
- Diskless (Flash-Based) Design for Improved Reliability
- Gigabit Ethernet Port for Out-of-Band Management.
- Runs IPS 5.x or CSC 6.x Code
- Can be Managed from the back Plane using Session or ASDM
- Four 10/100/1000BASE-T
- Four (Gigabit Ethernet Optical SFP 1000BASE-SX or LX/LH transceiver supported)
- The module extends the I/O profile of the Cisco ASA 5500 Series to a total of five Fast Ethernet and four Gigabit Ethernet ports on the Cisco ASA 5510, and eight Gigabit Ethernet ports and one Fast Ethernet port on Cisco ASA 5520 and 5540 appliances
Please view this Youtube videos by INEtraining.
Hope you like my post.An Introduction to Cisco ASA Firewall. Please share with others.
Also Check :-
Basic Cisco Router Configuration Commands
Basic Configuration required to access Internet through Cisco Router
An introduction to information security
An Introduction to Virtual Private Network ( VPN)