An Introduction to Cisco ASA Security Levels Concept :-
Cisco ASA platforms have some inherent security policies that are based on the relative trust or Security level that has been assigned to each interface. Interfaces with a higher security level are considered to be more trusted than interfaces with a lower security level. The security level scan range from 0 (the least amount of trust) to 100(the greatest amount of trust).
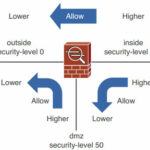
Usually the “Outside” interface that faces a public, untrusted network should receive security level 0. The “inside” interface that faces the community of trusted users should receive security level 100. An other ASA interfaces that connect to other areas of the network should receive a security level between 1 and 99.
The algorithm uses these security levels to enforce its default policies. For example, the interface connected to the public network should have the lowest security level, whereas the interface connected to the inside network should have the highest security level.
Here are the four default security policy rules for traffic as it flows through the appliance:-
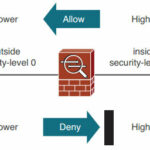
- Traffic flowing from a higher-level security interface to a lower one is permitted by default.
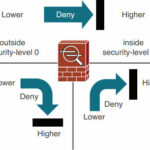
- Traffic flowing from a lower-level security interface to a higher one is denied by default.
- Traffic flowing from one interface to another with the same security level is denied by default.
- Traffic flowing into and then out of the same interface is denied by default
By default, the ASA allows packets from a higher (trusted) security interface to a lower (untrusted) security interface without the need for an ACL explicitly allowing the packets.
As you seen in the above image, if you need to comes from top to bottom, you have no need of any help. but in the case of lower to higer, you need a third party help. Same rule is going to be apply here. 🙂
For example, a user from the Internet who is trying to access an FTP server on the inside of your network is by default denied the connection. You could use a couple of methods to open a small hole in the firewall to allow this connection.
- Set up CTP ( Cut through Proxy) to allow the user’s connection.
- Use an access control list (ACL) to open a temporary hole.
If only a handful of outside users need access to the FTP server, CTP is an excellent method to use. However, if this is a public FTP server where people from the Internet are constantly accessing files in the server, and these people could be anyone in the world, CTP doesn’t provide a scalable solution.
Instead, you can use an ACL to open a temporary hole in the security algorithm to allow FTP traffic to the specific FTP server inside your network. In this sense, you are creating an exceptionto the appliance’s default security policy, which is to deny all inbound traffic by default.
You can assign a security level of 0 to 100 to an ASA interface with the fo l lo w i n g i n t erface configuration command :-
ciscoasa(config-if)# security-level level
From ASDM, you can set the security level when you edit an existing interface or add a new one.
By default, interface security levels do not have to be unique on an ASA. However, if two interfaces have the same security level, the default security policy will not permit any traffic to pass between the two interfaces at all. You can override this behavior with the same security-traffic permit inter-interface command.
In addition, there are two cases in which it is not possible to assign unique security levels to each ASA interface :-
- The number of ASA interfaces is greater than the number of unique security level values:-
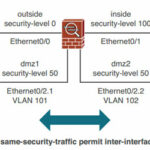 Because the security level can range from 0 to 100, there are 101 unique values. Some ASA platforms can support more than 101 VLAN interfaces, so it becomes impossible to give them all unique security levels. In this case, you can use the following command in global configuration mode so that you can reuse security level numbers and relax the security level constraint between interfaces.
Because the security level can range from 0 to 100, there are 101 unique values. Some ASA platforms can support more than 101 VLAN interfaces, so it becomes impossible to give them all unique security levels. In this case, you can use the following command in global configuration mode so that you can reuse security level numbers and relax the security level constraint between interfaces.
ciscoasa(config)# same-security-traffic permit inter-interface
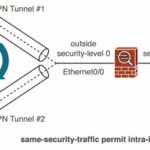
- Traffic must enter and exit through the same interface, traversing the same security level:-
When an ASA is configured to support logical VPN connections, multiple connections might terminate on the same ASA interface. This VPN architecture looks much like the spokes of a wheel, where the ASA interface is at the hub or center. When traffic comes from one VPN spoke and enters another spoke, it essentially enters the ASA interface and comes out of one VPN connection, only to enter a different VPN connection and go back out the same interface. In effect, the VPN traffic follows a hairpin turn on a single interface.
If an ASA is configured for VPN connections, you can use the following command in global configuration mode to relax the security level constraint within an interface.
ciscoasa(config)# same-security-traffic permit intra-interface
It’s too important to understand the Security level concept in Cisco ASA . i tried to define the all the process.
Hope you like my post.An Introduction to Cisco ASA Security Levels Concept. Please share with others.
Also Check :-
An Introduction to Cisco ASA Firewall
Basic Cisco Router Configuration Commands
Basic Configuration required to access Internet through Cisco Router
An introduction to information security
An Introduction to Virtual Private Network ( VPN)