How To do “Man in Middle” Attack using Ettercap in Kali Linux :-
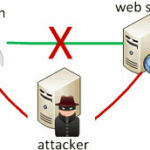
A man-in-the-middle (MITM) attack is a form of eavesdropping where communication between two users is monitored and modified by an unauthorized party. Generally, the attacker actively eavesdrops by intercepting a public key message exchange and retransmits the message while replacing the requested key with his own.
In the process, the two original parties appear to communicate normally. The message sender does not recognize that the receiver is an unknown attacker trying to access or modify the message before retransmitting to the receiver. Thus, the attacker controls the entire communication.
Sniffing traffic is particularly useful in gathering information from a target, because depending on the websites visited, you will be able to see the URLs visited, usernames, passwords, and other details that you can use against them.
How it Works :-
we used ARP poisoning with arpspoof and IPTables routing to manipulate traffic on our network destined for port 80 to be redirected to port 8080. The benefits of being able to perform this type of attack are endless because with it you can redirect secure ports to unsecure ports, redirect traffic to a specific port on a specific device, and so on.
In this tutorial i will use Ettercap along with Driftnet.
In this tutorial i am going to sniff my Wired network. However you can also sniff your Wireless network.
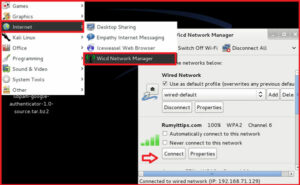
Go to the Application > Internet > Wicd Network Manager > Connect with your Wireless network.
Check my article :- How to Configure a Wireless Network Connection in Backtrack or Kali
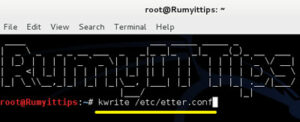
Now you need to be modify some setting in Ettercap configuration. Open the terminal and enter the following command.
| root@Kali:~# kwrite /etc/etter.conf |
now navigate to ec_uid , change the value 65534 to 0. as per below shown image.
and also remove the # from the If you use iptables.
Now Press the Ctrl + S to Save and Ctrl + Q to close the configuration editing.
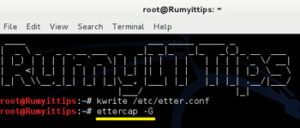
Now you need to open the Ettercap , on the same terminal , enter the following command.
| root@Kali:~# ettercap -G |
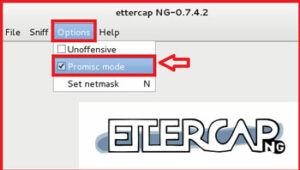
now go to the Options > select the Promisc mode.
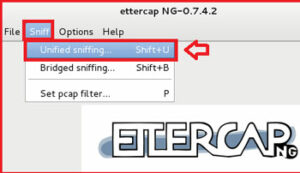
Now navigate to Sniff > Select Unified Sniffing .
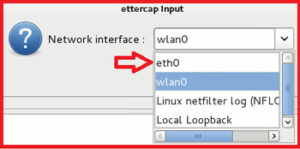
now choose your interface. i am going to select eth0.
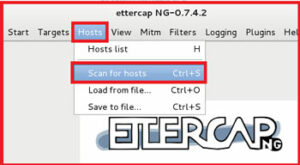
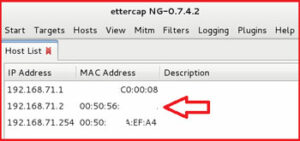
now navigate to hosts > select Scan for Hosts .
it will show you all available Host list including IP-address and Mac address.
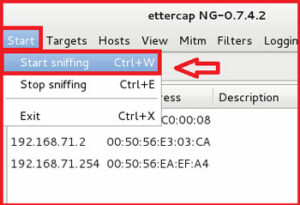
now click on the Start > select Start Sniffing .
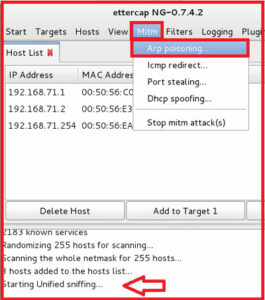
now go to Mitm ( Man in the middle attack ) and select he Arp Poising option.
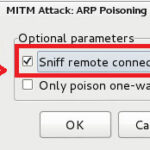
now select the ” Sniff remote connections ” option.
Now you need to be open the driftnet tool with the following command.
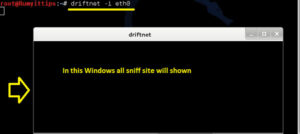
| root@Kali:~# driftnet –I eth0 |
it will comes with one driftnet windows. Now when any start browsing. this window will show you the image of visited URL.
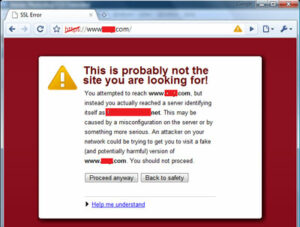
in case of HTTPS traffic, Victim or user will get certificate error. if the user ignore the message and proceed any way. then you are able to see the https traffic also.
Enjoy the Man-in-the Middle attack.
Also Check :- Cut off someone for test or for fun or for bandwidth
Note :- This tutorial is for Education Purpose only.
Hope you like my post.How To do “Man in Middle” Attack using Ettercap in Kali Linux. Please share with others.