How Hackers Gain Access To Your Computer :-
Viruses , Trojans , malware : these are the weapons of the Hacker. However, our carelessness is the actual strength of cyber criminals.
This is really big topic to write. i already write many articles on hacking and to protect privacy. Today i am trying to cover up some popular methods of hacking.
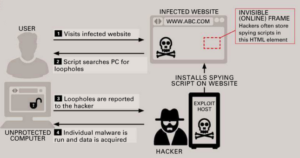
Drive By Downloads :- Hackers install spying scripts on websites and uses them to find out security loops in unprotected computers. The hacker then gets access to the unprotected computer using a malware and is able to acquire personal data in this way.
Drive-by Downloads are like great fishing nets for the hackers. Firstly, they fish for unprotected computers, then they acquire a huge amount of data. The Zeus Trojan is the most infamous malware in this category.
- Install an antivirus software
- Update operating system program regularly
- Always keep your browser plugins updated.
Man-in-the-Browser Attacks :-
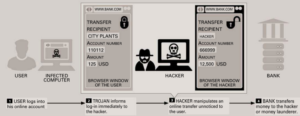
Hacking in real-time : in the so-called man-in-the-Browser attacks, a computer is infected with a Trojan First, which immediately forwards the users activities. in this way, the hacker can manipulate “live” online transfers and redirect any amount of money they want.
Hackers do not throw out their nets just in the ocean. if the victim appears to be particularly big fish, even a specific attack is worth while. With man-in-the-browsers attack, hackers can manipulate online transfers now – all of it in real time.
In 2009, the mysterious GhostNet caused a furor in the entire online world.
The Spy on the Internet :-
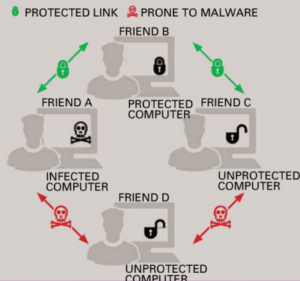
However, hackers catch the small and big fishes no just with viruses, worms or Trojans. Very often, internet criminals also use security loopholes in social networks such as Facebook. The advantage given to the cyber criminal ? A lot of the victims personal data is available here.
Check my articles on this topic :-
Stop Your Friends Infecting You On Facebook
Facebook introduces Trusted Contacts for recovering hacked account
Facebook security scan with ESET Social Media Scanner
Social Hacking :-
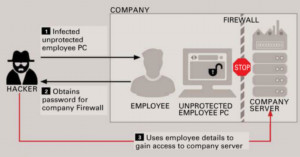
Even company or industrial spies use social networks very often as the starting point for their cyber attacks. The hacker will access sensitive company data via a poorely-protected employee PC,
and at the same time, they also get to know the relationship between employees. Psychologist name this strategy as “Social Engineering “.
The Careless User :-
Whether it,s Drive-by download , Man-in-the-Browser attacks or social hacking, cyber criminals wouldn’t have succeeded so triumphantly if not for the nativity for many users.
Splash Data , a provider of mobile security software, has listed the 25 most frequent passwords and passwords published on the internet.
Check my article on this topic :-
How to protect your passwords with LastPass
Six Ways to Make Your LastPass Account Even More Secure
The Underestimated Risk :-
Many users cannot imagine that they are targeted by the Data Mafia. “hackers can acquire data and passwords from poorly protected computers and even control them. Therefore, the careless users are the biggest and most trusted henchmen to internet criminals – those who are unwillingly and unknowingly connected to a gigantic botnet or as part of a chain of money launders

Also Check :-
Encrypt your Live Chat with Cryptocat
How to encrypt your cloud storage for free
Send notes that will self-destruct after being read
How to Stop Trackers From Tracking You Online
How to always start Google chrome in Private browsing mode
Hide your Real IP Location and Browse Anonymously
Encrypt Your Web Browsing with HTTPS Everywhere
How to Encrypt Your Email with Mailvelope
How to Browse Anonymously With Tor
Hope you like my post.How Hackers Gain Access To Your Computer. Please Share with others.